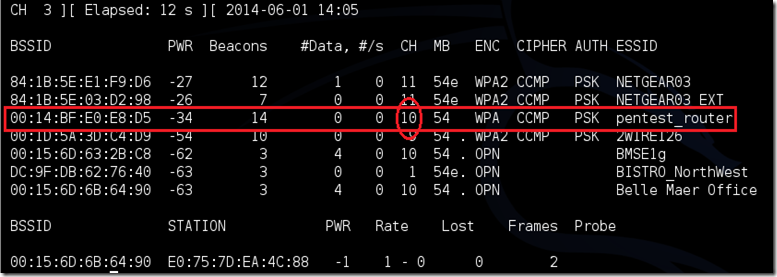
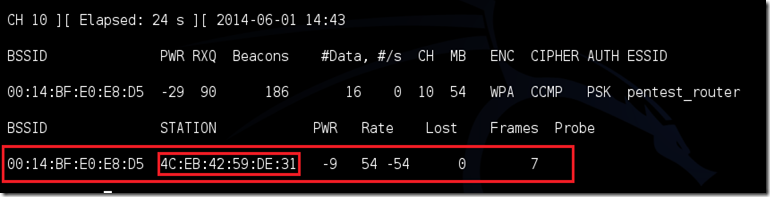
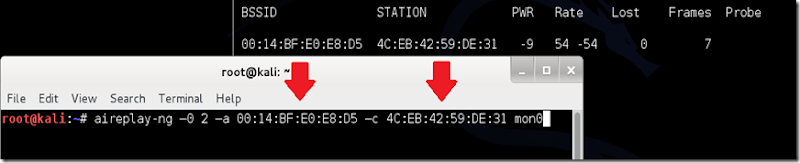
We all love Notepad++, luckily we can install this on Kali.
Step 1 – Install Wine
sudo apt-get install wine
*****
Step 2 – Download Notepad++
http://notepad-plus-plus.org/download/v6.6.7.html
Save
create new folder > Notepad – save the download in this folder
Step 3 – Use wine to open npp.6.6.7.Installer.exe
Open a terminal
cd notepad
ls
wine npp.6.6.7.Installer.exe
**If you’re on a 64 bit machine you’ll get an error about Multi Architecture instructions.
Okay, so lets fix this, and make your machine able to cope with multiple architectures.
Step 4 – Make 64 bit machines “Multi Architecture”
In a root terminal type
dpkg –add-architecture i386
apt-get update
apt-get install wine-bin:i386
Now, lets try step 3 again.
Now the wine installer runs
Okay > Next > I Agree
Accept defaults in Setup
Next > Next >
Tick the box to create a shortcut on the desktop
Install > Finish > Run Notepad++
Here’s your shortcut..
Viola! Easey Peasey
*****